Earlier this week I noticed that Google searches on my Windows XP box were coming up with bizarre results. I'd type something in to Google and my search results would come up with headings and descriptions that looked correct but linked to bogus sites. At first I thought that this was some kind of search engine optimization gone awry. Two things changed my mind:
- I noticed my web browser accessing a bogus URL: http://1.2.3.0
- I checked my other machines (all running Linux) and they all worked correctly.
I opened up a Cygwin bash prompt and tried to ping 1.2.3.0, thinking that perhaps this was redirecting elsewhere - nothing turned up. On the other hand, if I launched Firefox and typed in that URL, it would connect to a server and retrieve some JavaScript. At this point I was convinced that this redirection was localized to my Firefox process.
I decided that whatever was causing this could have a varying degree of sophistication. Going for the low-hanging fruit seemed to be the most obvious course of action. I fired up Process Monitor from Sysinternals and logged everything that happened in the system as I entered "http://1.2.3.0" in the Firefox address bar. Here's what I found:
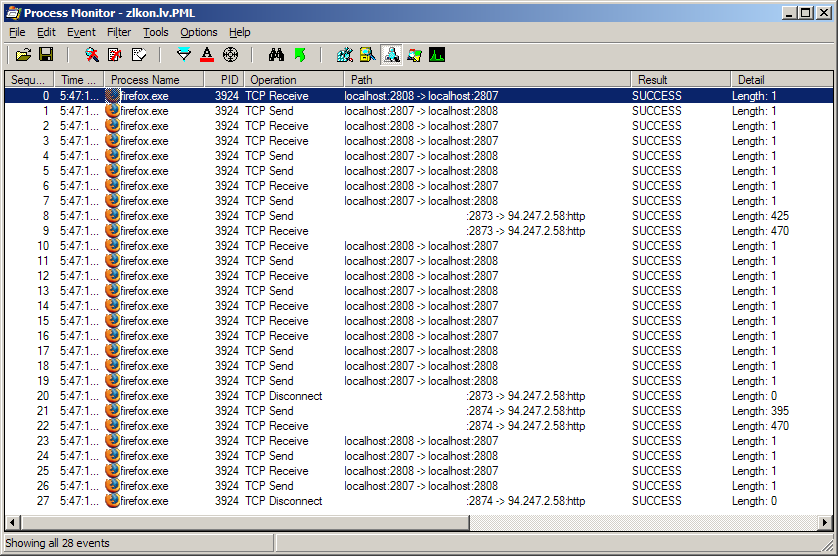
Notice the TCP transmissions to 94.247.2.58 port 80 (HTTP). Something is definitely phoning home. A quick run of the ping command with reverse DNS lookup gave me a successful hit of hs.2-58.zlkon.lv.
Rather than continuing with a fine-grained investigation, it was time to let my fingers do the walking. I had already disabled (though not yet eradicated) this malware, and at this point I had something to search on. Google promptly returned these juicy nuggets:
Beware of sysaudio.sys!
Fake sysaudio.sys causes search engine hijack
It looks like whatever put this on my machine was using some kind of unpatched browser exploit. Anyway, those blog posts point out that c:\windows\system32\sysaudio.sys is the likely culprit. Sure enough, I found it on my machine.
I decided to take a look to see if I could obtain some more information from this binary without doing any disassembly. I ran the strings command and got some interesting results. I won't include them all here, but I will note that they were all reversed in the binary. For example, one line in the strings output was:
:tnegA-resU
Look familiar? Reverse the string and think HTTP. ;)
Among other things, there are HTML script tags embedded in the binary, as well as parts of a URL that look like they are eventually spliced together. There's also a line containing the string "ntnet.drv", so that looks like another file that might be involved.
Here's the MD5 checksum for sysaudio.sys: db8c035980bf8cd18953e3f3f0abfe7e
By quarantining the files and fixing the registry key as mentioned in those blog references, it appears that this piece of malware has been eliminated. Despite the fact that I was happy (and intrigued) to track this issue down, I am kicking myself in the ass for allowing this to happen in the first place. On Windows I tend to run as an Administrator because of so many shitbox apps out there that can't handle a low-privileged user. I usually use Michael Howard's DropMyRights utility to ensure that stuff like this can't happen. I don't know why I wasn't using it on Firefox... perhaps my modified shortcut got overwritten during an upgrade?
UPDATE January 9, 2009: I submitted this malware sample to a number of anti-virus vendors, and some of them needed to add it to their databases. It appears that a slightly different version has been floating around as of late, this time under the guise of c:\windows\system32\wdmaud.sys and accessing http://7.7.7.0 instead of http://1.2.3.0.



